Table of Contents
You need an Azure App Registration for EagleEye deployment.
Step 2.1 - Create the App Registration
- Go to Azure Portal → App registrations → New registration

- Enter the app name:
SSW.EagleEye.Master - Set Supported account types to: Accounts in this organizational directory only
- Click Register

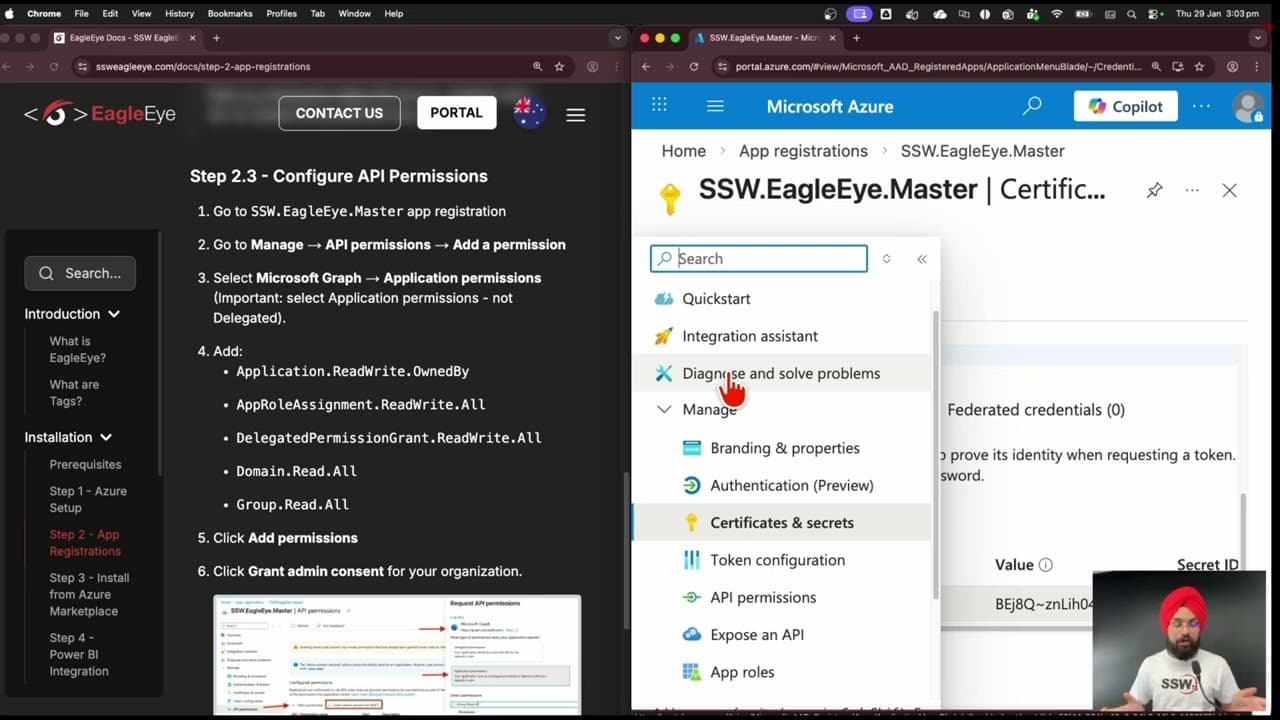
Step 2.2 - Create a Client Secret
- Go to Certificates & secrets
- Click New client secret
- Add a description (e.g.,
Master Secret) - Select an expiry period → Add

- Copy the secret value immediately (you will need this later; it will never be shown again)

Warning: After deployment, remove the secret value from any temporary notes (clipboard, notepad, etc.).
Do not delete the secret from Azure
Step 2.3 - Configure API Permissions
- Go to
SSW.EagleEye.Masterapp registration - Go to Manage → API permissions → Add a permission
- Select Microsoft Graph → Application permissions (Important: select Application permissions - not Delegated).
- Add:
Application.ReadWrite.OwnedByAppRoleAssignment.ReadWrite.AllDelegatedPermissionGrant.ReadWrite.AllDomain.Read.AllGroup.Read.All
- Click Add permissions
- Click Grant admin consent for your organization.
